- 1234-5678-9011
- [email protected]
- Jalan Cempaka Wangi No 22
OUR SOLUTIONS
OUR SOLUTIONS
ARKODIA IT
At ARKODIA INTEGRA TEKNOLOGI, we offer a comprehensive range of Network Cyber Security IT solutions designed to meet the unique needs of your business cyber security.Our services are tailored to provide you with the tools and support you need to thrive in a technology-driven world.
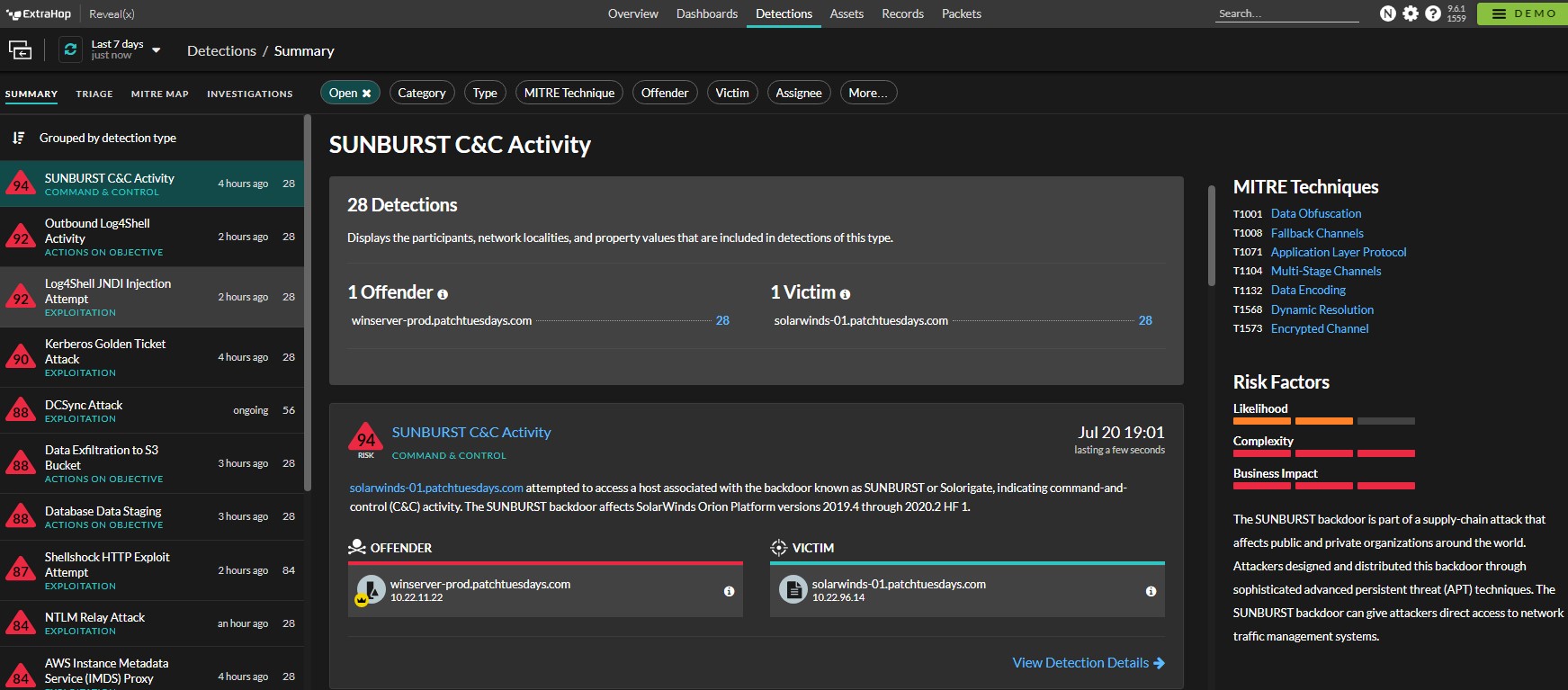
NDR / Network Detect and Response
A solution that uses a combination of non-signature-based advanced analytical techniques such as machine learning to detect suspicious network activity. This enables teams to respond to anomalous or malicious traffic and threats that other security tools miss.

FDR / Firmrware Detect and Response (Supply Chain Security)
A solution that protects below the OS and the BIOS, securing the core infrastructure code for components and devices and a protection from supply chain cyber security attack.
- Threat Detection and Response: Proactive monitoring and quick response to security threats.
- Data Protection: Encryption and data loss prevention solutions to secure your sensitive information.
- Compliance Management: Ensure your business meets industry standards and regulatory requirements.
DSPM / Data Security Posture Management
A solution that provides visibility as to where sensitive data is, who has access to that data, how it has been used, and what the security posture of the data stored or application is. It does that by assessing the current state of data security, identifying and classifying potential risks and vulnerabilities, implementing security controls to mitigate these risks, and regularly monitoring and updating the security posture to ensure it remains effective.
- IT Strategy Development: Align your IT initiatives with your business goals.
- Infrastructure Assessment: Evaluate and optimize your current IT infrastructure.
- Technology Roadmap: Plan for future technology needs and investments.

Secure Web Gateway
A solution that protects Web-surfing PCs from infection and enforce company policies by filtering unwanted software/malware from user-initiated Web/Internet traffic and enforces corporate and regulatory policy compliance.
- 24/7 Monitoring and Support: Round-the-clock monitoring and support to ensure your systems are always up and running.
- Patch Management: Regular updates and patches to keep your systems secure and up-to-date.
- Backup and Recovery: Reliable backup solutions and disaster recovery plans to protect your data.
Enterprise Backup and Recovery
A solution that captures a point-in-time copy (backup) of enterprise workloads in on-premises, hybrid, multicloud and SaaS environments that has many backup security features such as; Early threat Detection, Proactive Threat Hunting, Avoid Reinfection, Automate Clean Recovery, and many more.
- Custom Applications: Design and development of bespoke software applications.
- Mobile Apps: Development of intuitive and high-performing mobile applications.
- Integration Services: Seamless integration of new software with your existing systems.


Network Packet Broker
A solution that provides high-performance network visibility solutions to allow seamless administration of security solutions, performance management, and network monitoring. Niagara Networks products provide advantages in terms of network operation expenses, downtime, and total cost of ownership.
- Network Design and Implementation: Design and setup of efficient and scalable network infrastructure.
- Network Security: Implementation of security measures to protect your network from threats.
- Network Management: Ongoing monitoring and maintenance of your network to ensure optimal performance.
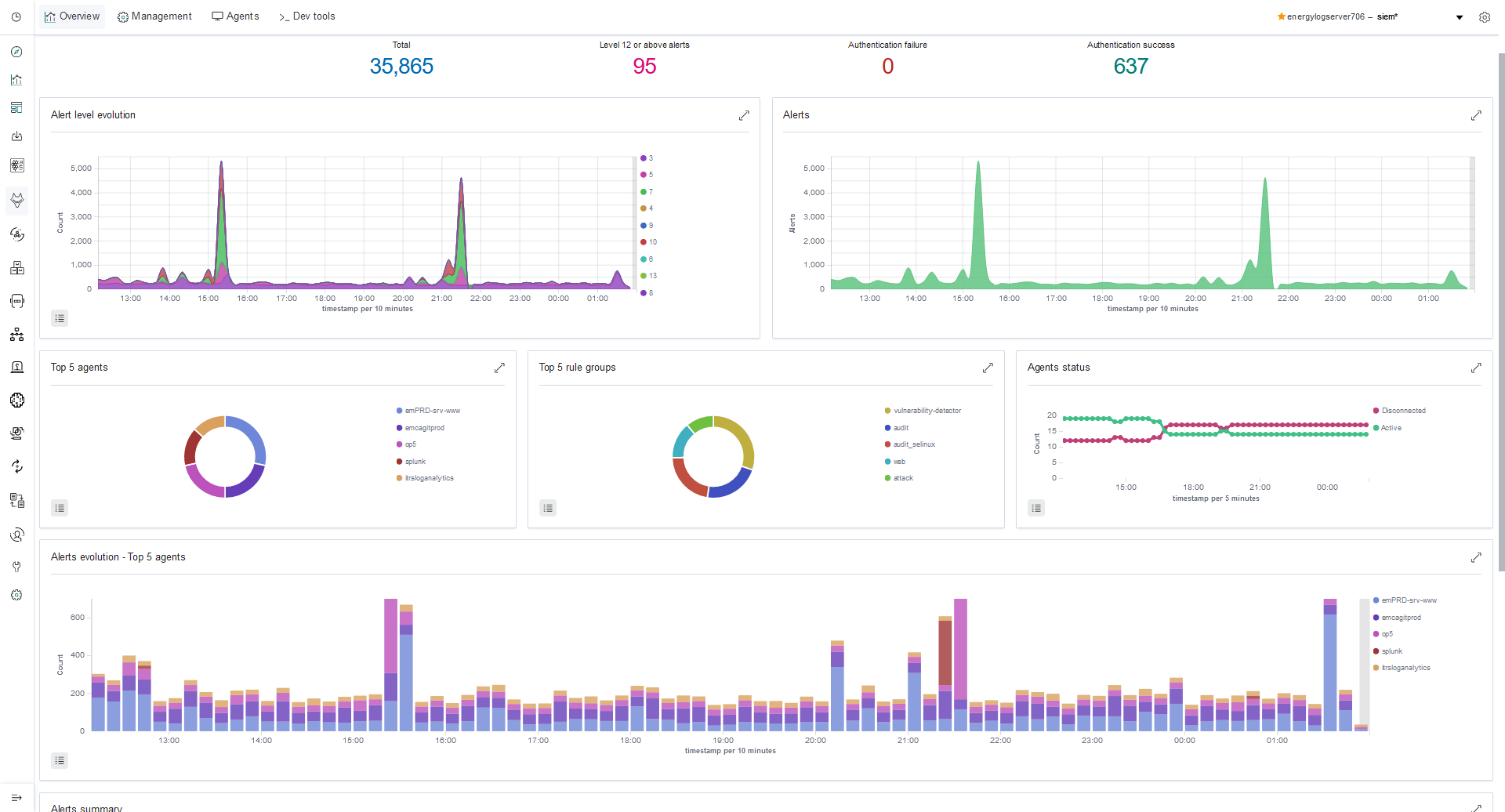
Next-Gen SIEM
Energy Logserver (often called ‘poor man’s Splunk’) is a comprehensive platform designed for the centralized collection, correlation, and analysis of data from IT environments. Built upon the Elasticsearch engine, it offers scalable and efficient data storage and retrieval, making it suitable for organizations of all sizes.
- Custom Applications: Design and development of bespoke software applications.
- Mobile Apps: Development of intuitive and high-performing mobile applications.
- Integration Services: Seamless integration of new software with your existing systems.

Mobile App Protection Security
A Solution that is specializing in mobile application security solutions. A total mobile app security solution that provides anti-tampering, code obfuscation, and real-time management features to safeguard applications from hacking attempts.
- Network Design and Implementation: Design and setup of efficient and scalable network infrastructure.
- Network Security: Implementation of security measures to protect your network from threats.
- Network Management: Ongoing monitoring and maintenance of your network to ensure optimal performance.
Identity Access Management & Identity Governance and Administration
A cybersecurity solution designed to secure user access to applications, data, and systems by managing authentication, authorization, and identity verification. It ensures that only the right people can access the right resources at the right time, enhancing security while improving user experience.
- Custom Applications: Design and development of bespoke software applications.
- Mobile Apps: Development of intuitive and high-performing mobile applications.
- Integration Services: Seamless integration of new software with your existing systems.


Threat Simulation & Testing
A solution for Breach and Attack Simulation (BAS) platform designed to help organizations proactively test and strengthen their cybersecurity defenses. By emulating real-world cyber threats in a controlled environment, it enables security teams to identify vulnerabilities, validate the effectiveness of security measures, and receive actionable remediation guidance.
- Network Design and Implementation: Design and setup of efficient and scalable network infrastructure.
- Network Security: Implementation of security measures to protect your network from threats.
- Network Management: Ongoing monitoring and maintenance of your network to ensure optimal performance.
